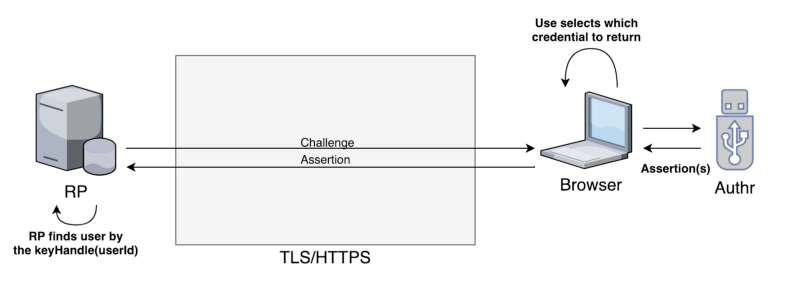
In this scenario we have removed the need for both usernames and passwords. The WebAuthn flow is very similiar to the paswordless flow, but when registering we require the resident key option. User account selection is handled by the client/authenticator. If multiple credentials are found, the user will be able to choose which credential to use.
Note: When we say passwordless, what we mean is that no password is sent over the internet or stored in a database. Password, PINs or Biometrics might be used by the authenticator on the client